Seems like the digital fortress that is OS X is finally starting to crack. Andrew over at the Ambrosia Software Web Board writes about what he sees as a Trojan for OS X which was postet at the MacRumors.com website.
It’s a little compressed file pretending to include screenshots of the next OS X version. When decompressed it appears to include a JPG file which in reality is a UNIX executable that performs several malicious functions.
From what he found out the Trojan tries to send itself via iChat to all your buddies, there is also code that tries to spread the Trojan via eMail but it looks like it’s not entirely finished.
Read more about the dissection in the original thread » here. Included is also a disassembled version (textfile) of the Trojan.
Here is the thread at MacRumors.com (link to the original file deleted).
So maybe it’s time for us Mac users to start running a virus scanner in the background while working?
Update: robg of macosxhints.com examined the Trojan a little further for Macworld at Digging deeper into the Leap-A malware. His resum??is the following:
I am now officially very sick of Leap-A, having spent probably 18 hours on it over the last two days. The short summary is that it’s a bad piece of malware that could have been worse but it’s far from the self-propagating internet-spreading virus/worm that’s been described on other sites. At the end of the day, it’s really just a good reminder to be very careful about what you download and install on your Mac.
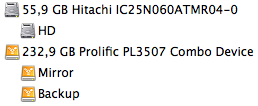 Next I partitioned the hard drive (using HFS+ for maximum compatibility under OS X) with one partition serving as the mirror for my internal 60GB disk. The rest of the disk is used as backup space for other data, right now we’ll only care about the mirror drive.
Next I partitioned the hard drive (using HFS+ for maximum compatibility under OS X) with one partition serving as the mirror for my internal 60GB disk. The rest of the disk is used as backup space for other data, right now we’ll only care about the mirror drive.
 The
The